Radiator Policy Server
Radiator Policy Server is a next-generation network Authentication, Authorisation and Accounting server aimed at enterprise customers. Powered by Radiator 10, an overhauled policy engine.
Written in Rust, Radiator Policy Server achieves concurrency, high performance and security. Up to the latest standards and with great variety of integration options. Easy to manage and operate.
Radiator Policy Server also brings ease of operations with a monitoring and management dashboard, as well as a REST API for upstream and downstream integration.
Basic information
- Fully featured RADIUS support
- TACACS+ support
- Secure and reliable RADIUS proxying using RadSec, with TLS 1.3
- Roaming and proxying support (eduroam, OpenRoaming)
- Supports IPv4, IPv6, UDP, TCP
- Consumable upstream/downstream REST API
- Extensible with wide range of logging solutions (JSON, syslog, Elasticsearch, Splunk, etc.)
- Support for 802.1X wireless authentication
- Support for wide range of EAP authentication methods MD5, OTP, GTC , TLS, TTLS (including PAP, CHAP, MS-CHAP and MS-CHAPv2), PEAP and TEAP
- TLS 1.3 for EAP-TLS, EAP-TTLS and PEAP and TEAP
- Support Multi-Factor Authentication (MFA, 2FA): HOTP and TOTP, Yubikey tokens, Duo Security, RSA Authentication manager
- Comes with built-in SQLite
- Supports SQL backends (MySQL, MariaDB, PostgreSQL)
- Aruba MPSK support
- Cisco iPSK support
- Lua scripting support without compromising performance
- Integrates with Microsoft Entra ID both Device Code Flow and Resource Owner Password Credentials (ROPC), and Microsoft Graph API
- Debugging and packet capture creation
- Supports LDAP backends (Active Directory, OpenLDAP, etc.)
- Supports Active Directory integration with LDAP, NTLM
- Supports integration with various REST APIs and HTTP-based backends
- CoA (RFC5176)
- Direct or applicable dictionary support with RFCs 2486, 2548, 2607, 2759, 2809, 2865-2869, 3162, 3447, 3579-3580, 3748, 4137, 4226, 4372, 4603, 4648, 4675, 4679, 4818, 4849, 5080, 5216, 5246, 5247, 5281, 5904, 5997, 5998, 6158, 6238, 6519, 6572, 6613, 6614, 6911, 6929, 6930, 7055, 7056, 7170, 7268, 7585, 7930, 8044, 8559, 9190, 9427. See latest RFC support list from our RFC search tool.
Dashboard
Dashboard
Radiator Core and Radiator Policy Server feature a dashboard for monitoring. The main dashboard shows you overall information about server statistics. Graphs can be filtered to show desired handlers.
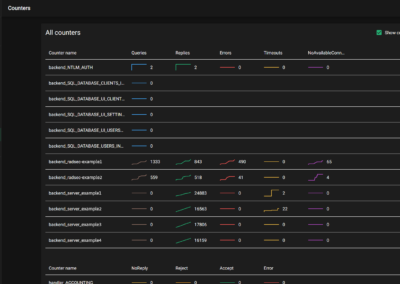
Counters
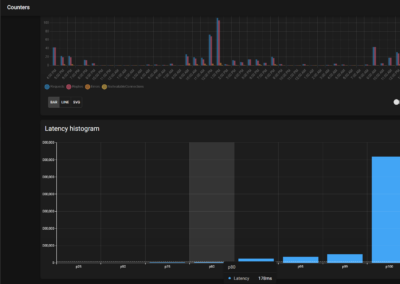
The user interface shows you counters for all handlers. Clicking any counter will show graph for specific counter, with more information on accepts/rejects, requests/responses, as well as information like latency.
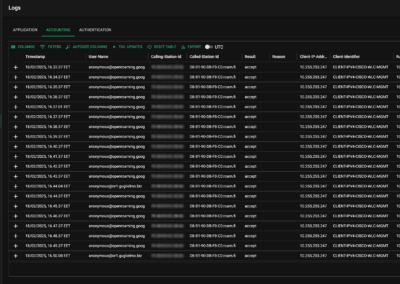
Log viewer
The user interface displays authentication, accounting and application logs. Logs column can be filtered and re-ordered locally to fit employee role.
Popular use cases
Enterprise Wi-Fi authentication
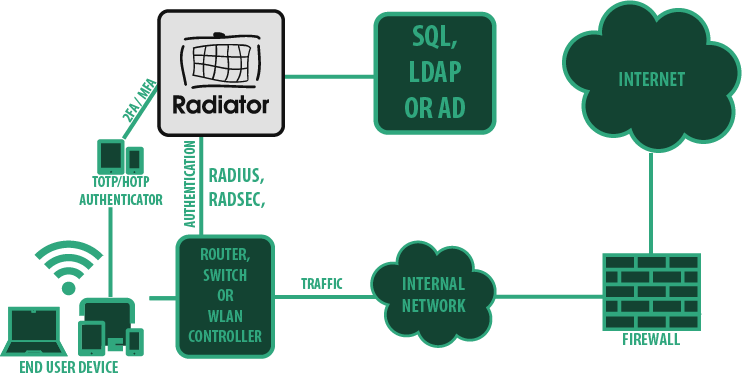
One of the basic use cases for RADIUS authentication is employee LAN authentication, meaning employee’s authentication to both company’s internal network and the world wide web. There are multiple methods to achieve secure network connection for your employees.
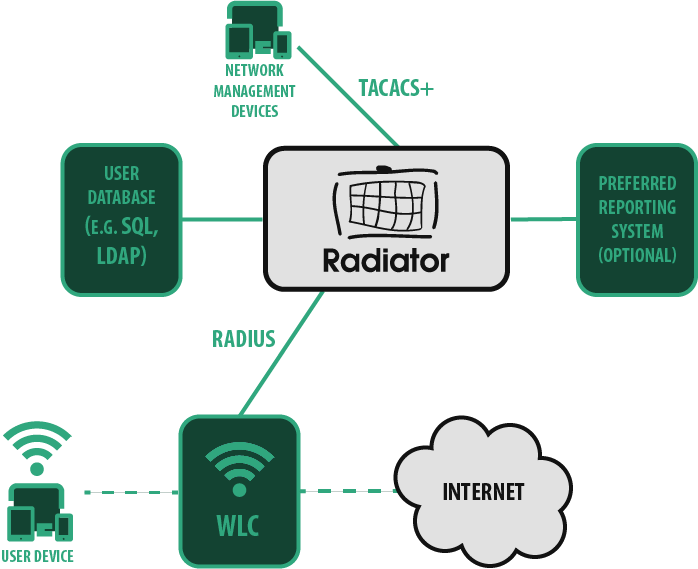
At its simplest, the employee logs in with username-password combination. The network access server sends request to Radiator which checks credentials against an SQL database. Matching credentials grant access, request with wrong credentials is rejected. This solution requires local IT admin to provision WiFi credentials. The adjacent diagram showcases some of the many pieces Radiator can integrate with in this use case, for example Active Directory or an SQL database.
When using AD the user credentials are checked against AD credentials. This model does not require manual configuration of first connection. The solution can also be complimented with second authentication factor with TOTP. All this can be implemented with just Radiator and your database of choice.
Device administration (TACACS+)
A classic use case for an AAA server is to manage administrative access to network devices such as controllers, switches and network gateways. Device administration for various types of NAS can be done with RADIUS or TACACS+ protocols.
With Radiator, you can get rid of insecure shared passwords and implement role-based access with personal user accounts. For easy user management, Radiator integrates external LDAP and SQL backends for fetching the user information and privileges. User authentication can also be combined with various MFA options for further security.
The choice between RADIUS and TACACS+ depends on security requirements in your organisation and the protocols supported by your device vendor(s). TACACS+ adds more encryption and allows more granular control for authorising each command separately, but not all devices support it. Radiator can be configured to process both RADIUS and TACACS+ requests, so you can choose one or both.
With Radiator, you can avoid vendor lock-in and freely choose the network equipment you want: Radiator includes vendor-specific attributes from over 150 vendors and adding proprietary ones or own custom attributes is made easy. This makes Radiator a great choice for multi-vendor environments.
Looking for more?
More information Radiator Core:
Already got a licence?
Radiator Policy Server reference manual (.html version)
Radiator Policy Server configuration guide (.html version)